Security Settings
In the Security section of the Organization Management page, administrators can configure a wide range of security settings for the organization. These include:
- Restrictions on Contacts visibility
- Rules for joining the organization
- Screen watermarking
- Download permissions for attachments
- Encryption policies
- Password-free verification
You can also control whether regular users are allowed to create apps, API libraries, or develop plugins.
Rules for Joining the Organization
Navigate to [Org Admin] > [Security] > [Account] to define access rules when users join the organization, including approval policies and required identity information.
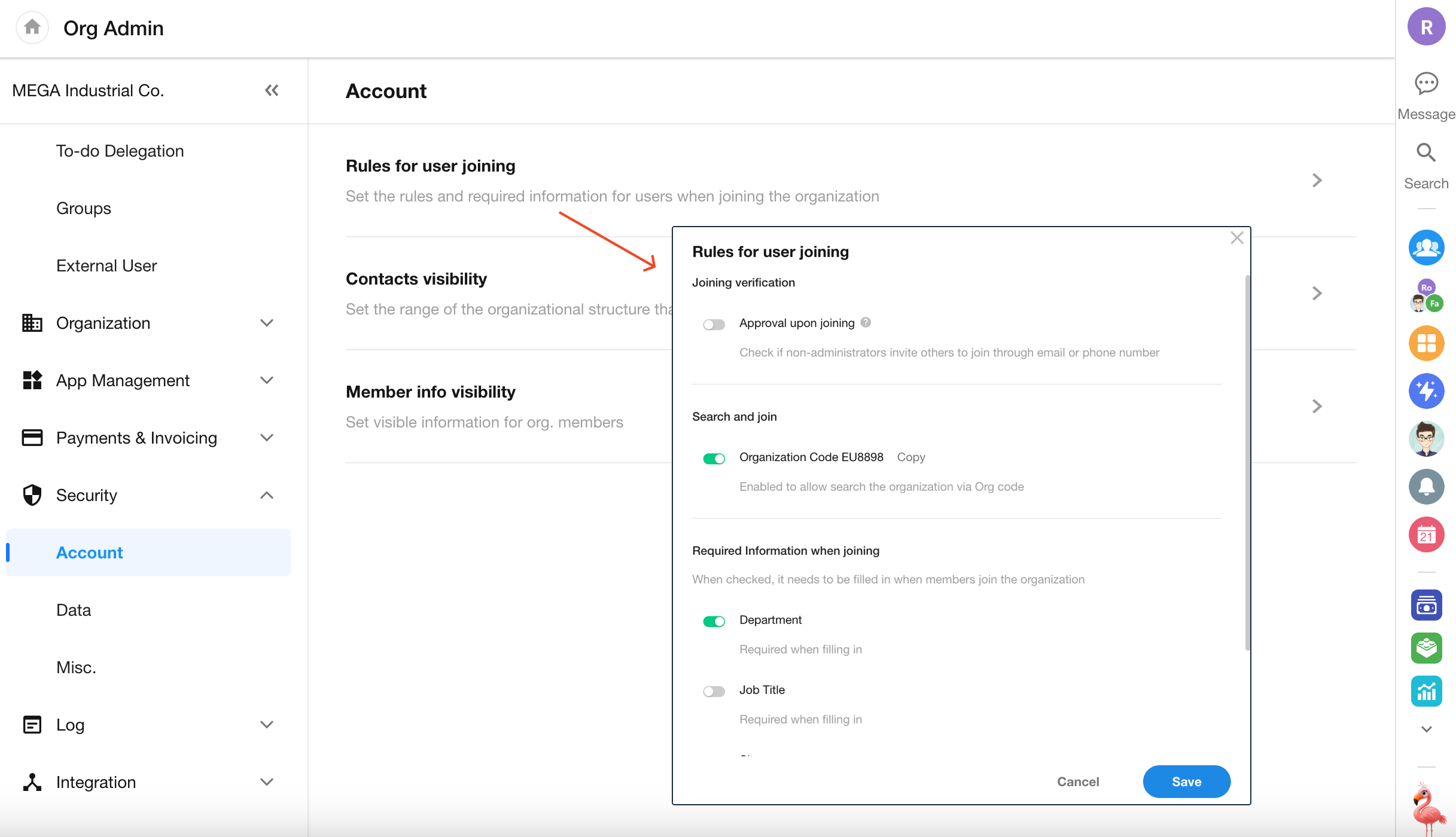
Approval Upon Joining
-
When approval is enabled:
If a non-admin invites someone via mobile number or email, the invited user must be approved by an organization admin after registration. -
Scenarios that never require approval:
If an organization admin invites a user via mobile number or email, the invitee joins the organization directly after registration—no approval needed. -
Scenarios that always require approval:
- When a user registers via a public invite link, approval is mandatory.
- When a user searches for the organization code to request access, approval is also required.
Joining via Door ID
When enabled, users can search for your organization by entering the organization door ID and request to join.
When disabled, even if the organization door ID is known, users will not be allowed to request to join.
Required Information Upon Joining
You can configure mandatory fields that users must fill in when requesting to join the organization, such as:
- Department
- Job Title
- Employee ID
- Work Location
Set Contacts Visible to Members
Organization Admin can set which contacts are visible to members.
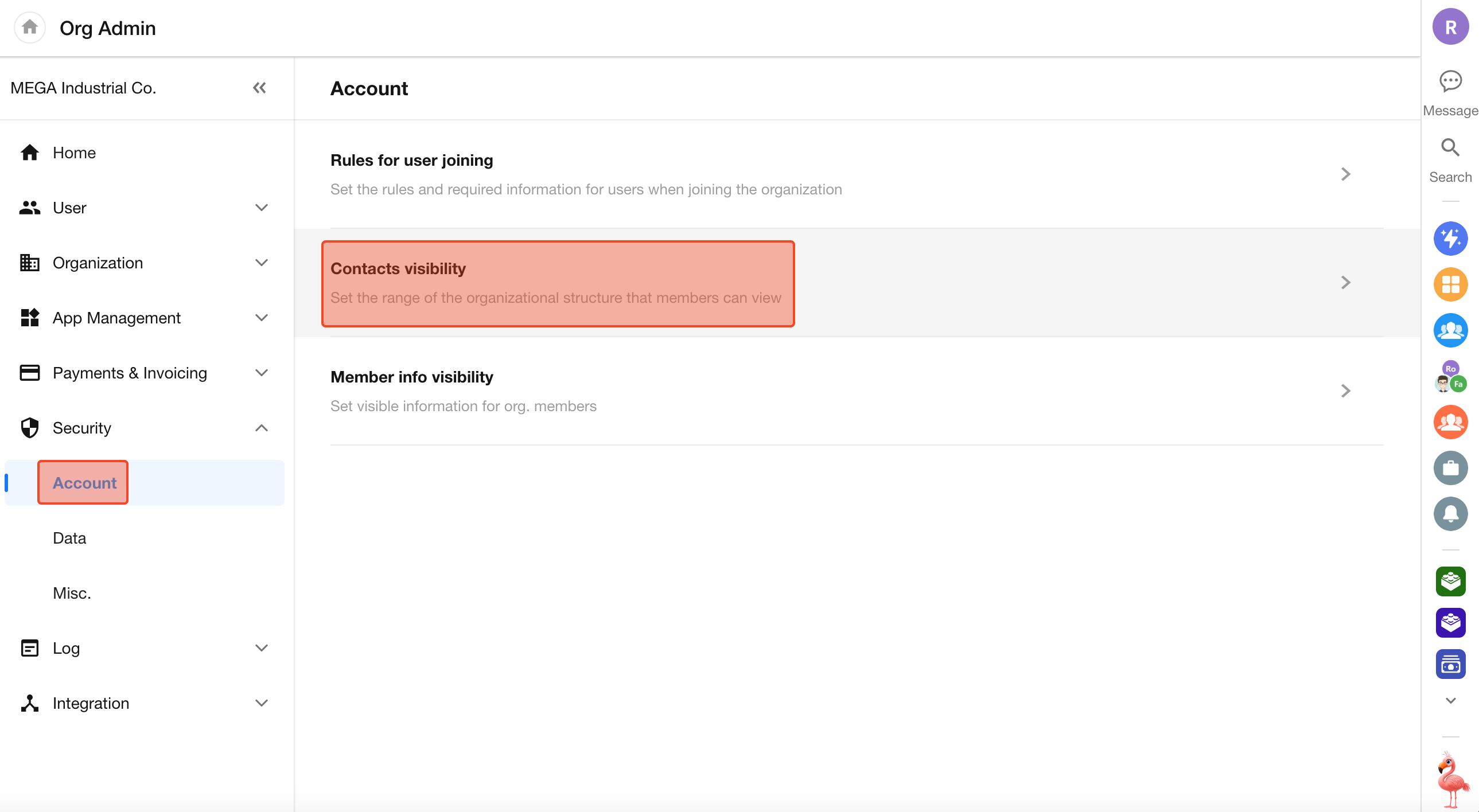
Set Rules
It is possible to set the following two kinds of rules:
-
Restricted from viewing contacts in other departments
Selected members can only view contacts in their department (including members and department structure). Organization Admin can also set whitelists and add members from other departments.
-
Restricted from viewing all contacts
Selected members cannot view all contacts in the organization, including members and department structure. Organization Admin can add some members to whom the contacts are visible.
Use Case
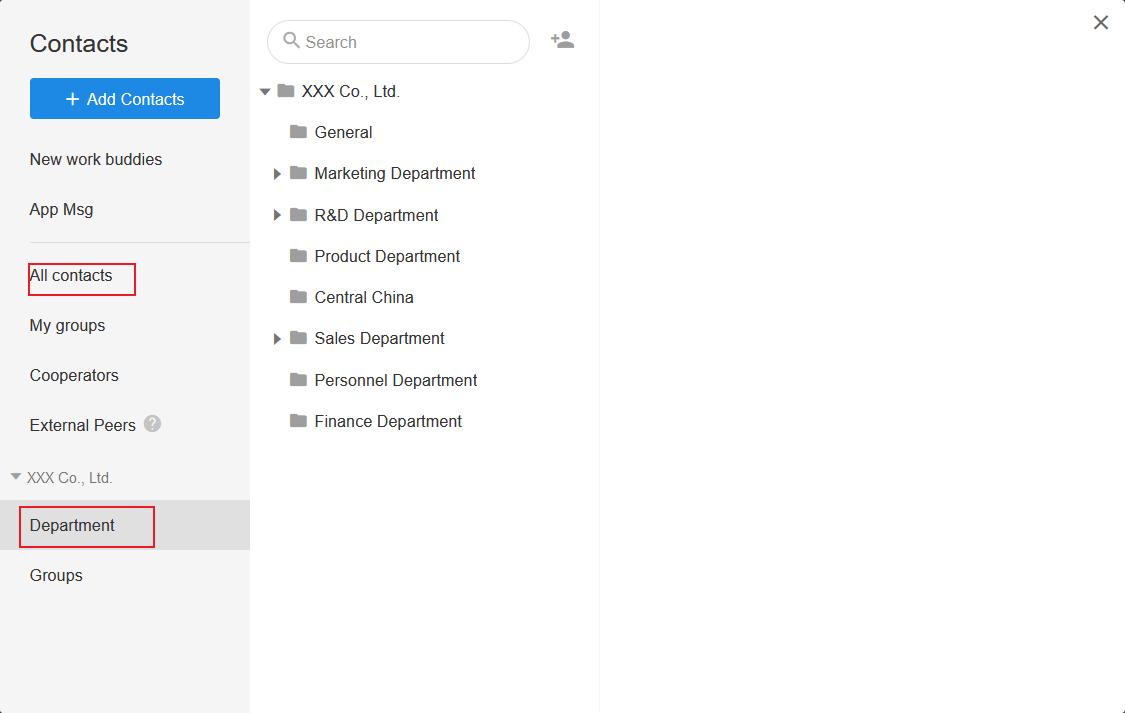
Example 1:Restricted from viewing contacts in other departments
Ross (in the R&D Dept.) and members of the Sales Dept. can't view contacts in other departments, but they can view members of the Personnel Dept. and Lan, the accountant in the Finance Dept.
-
Create a rule
-
Select Ross and Sales Dept. in [Only the contacts of this department can be viewed].
-
Add Personnel Dept. and Yao in [Additional visible members].
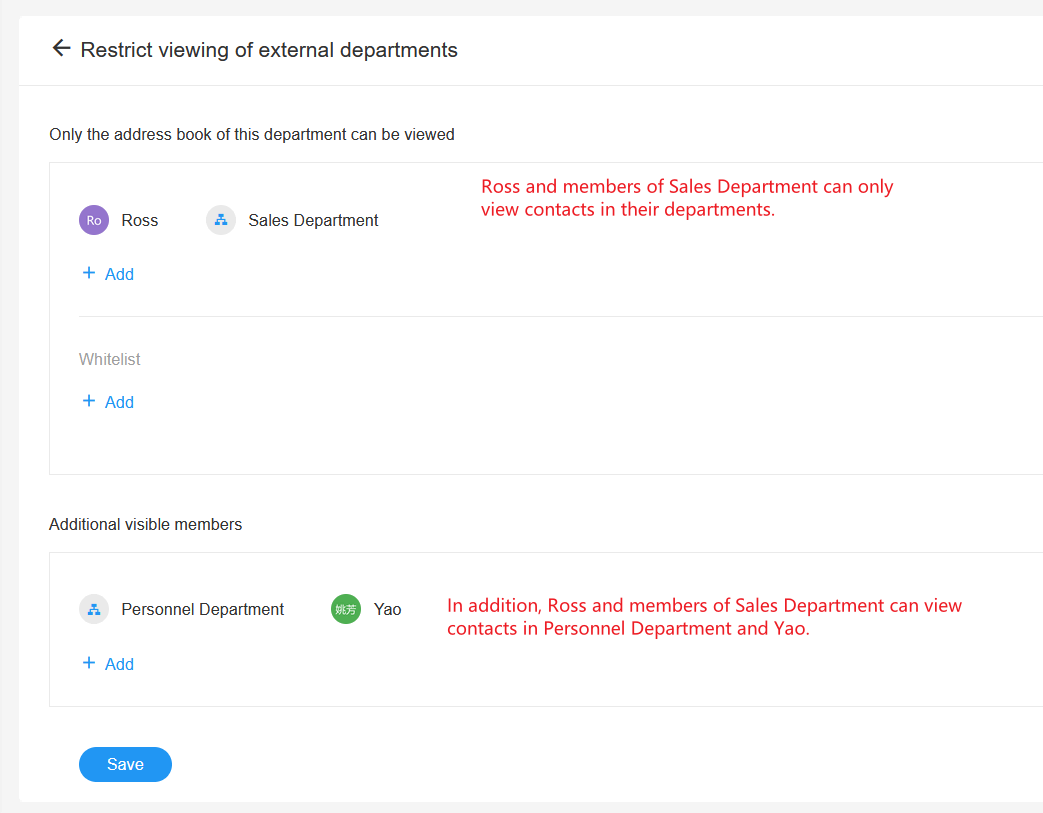
(It should be noted that the Finance Department that Lan belongs to is hidden, so Lan is only viewable in [All Contacts].)
Whitelist
If you choose to restrict a department or o-role, and select somne members to be whitelisted, then the whitelisted members are not restricted by the rules.
For example, if Super Admin belongs to the Sales Department, then Super Admin should be whitelisted, otherwise Super Admin will also be restricted from viewing.
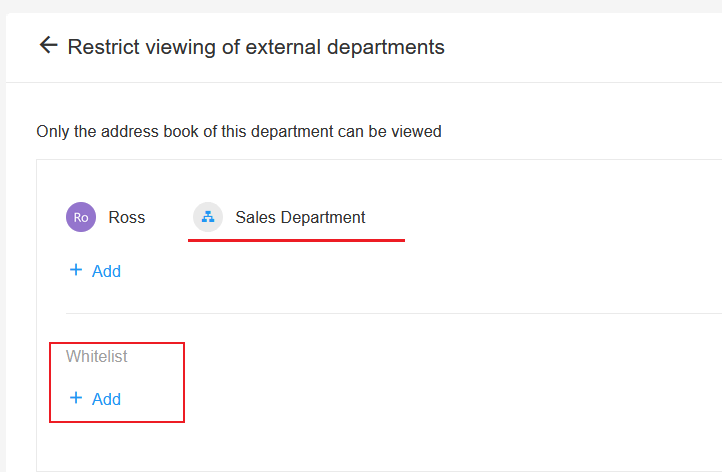
Example 2: Restricted from viewing all contacts
If your agents joined the organization, they become colleagues and can chat and view contacts, which is generally not allowed. You can set a rule to restrict these agents from viewing pthers' contacts.
-
Create a rule
-
Select agents by o-role in [Restrict viewing of everyone]. If there are some agents that are not to be restricted, you can set a whitelist.
-
Add members visible to the agents in [Additional visible members], except these members, other contacts are not visible to the agents.
If hide some contacts
-
In [Contacts], if you view members by all or by department, the quarantined contacts will not be visible.
-
In posts or discussions, if you want to select and mention a member, the quarantined contacts will not be visible.
-
When adding members, the quarantined contacts and departments will not be visible.
Priority of Rules
1. For single member and the department they belong to
Rules for single members are prioritized over rules for their departments.
For example, if in Rule 1, Ross can view the Personnel Department, while in Rule 2, the Personnel Department is not visible to Ross's department.
In such case, Ross can view the Personnel Department.
2. For superior and subordinate departments
-
Setting 1: only the superior department is selected, not the subordinate department
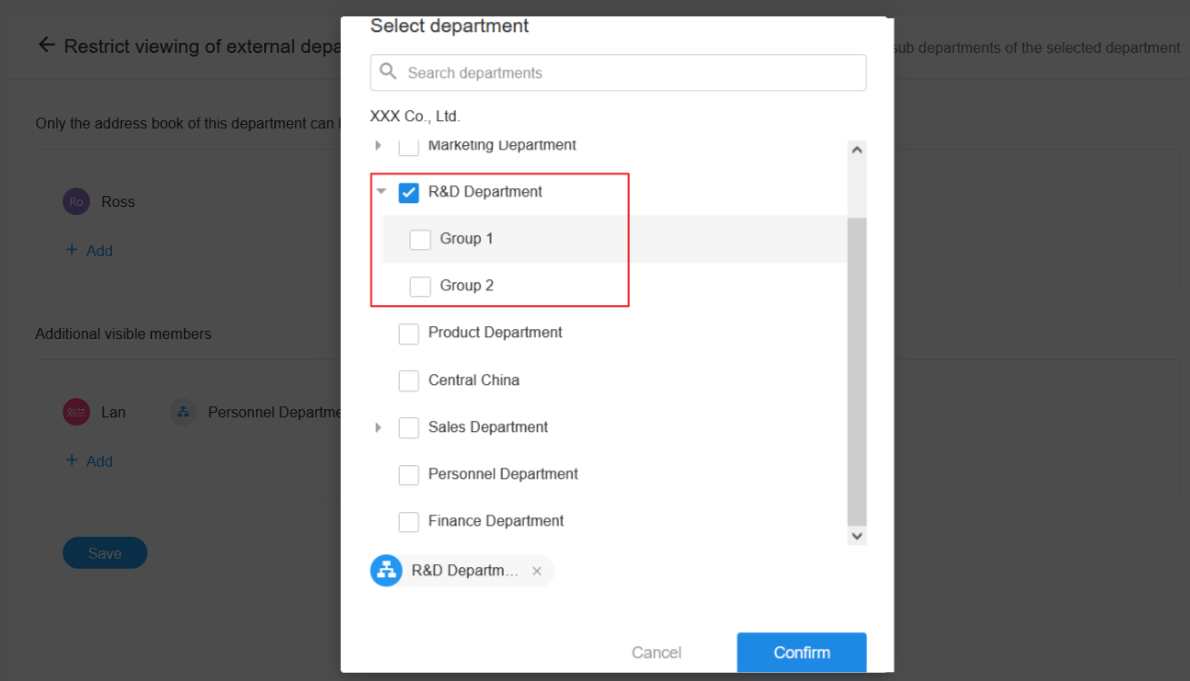
As in the above rule, only the R&D Department is checked , then the R&D Department has the same permissions as the sub-departments, which means that the sub-departments can view the same contacts as the R&D departments. Members of Group 1, Group 2, and R&D Department are only able to view the contacts of these three departments.
-
Setting 2: Both superior and subordinate departments are selected
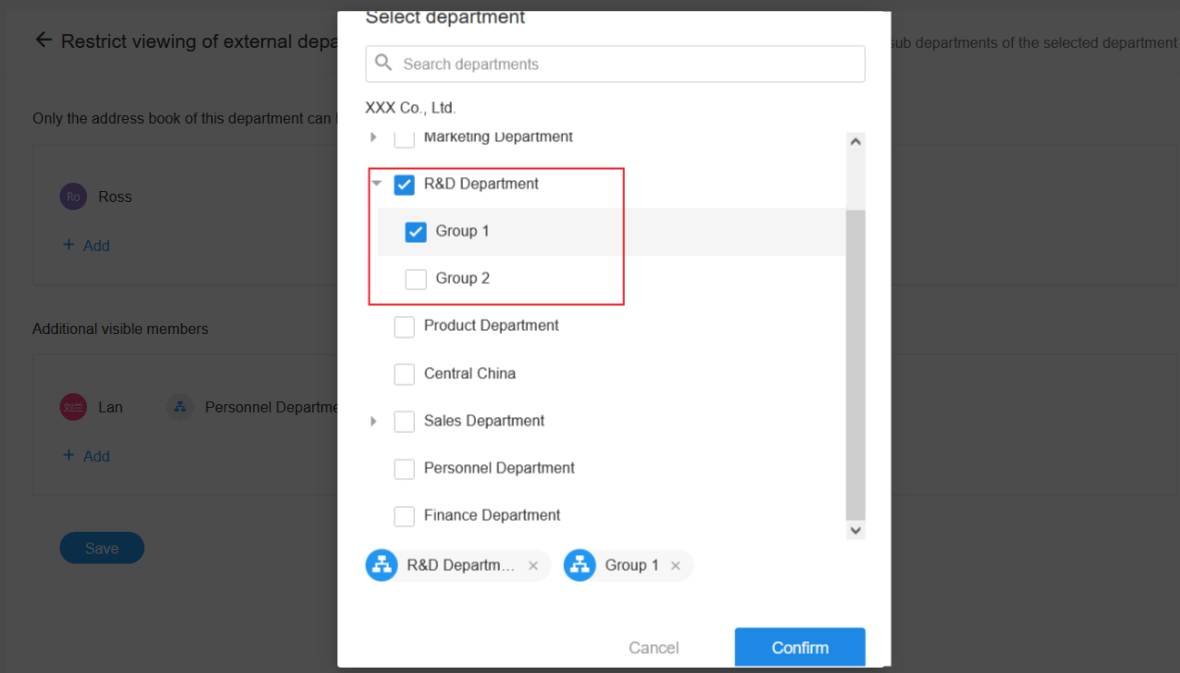
As above, both R&D Department and Group 1 are checked, then Group 1 follows its own rules.
Members visible to R&D: [R&D Department, Group 1, Group 2]
Members visible to Group 1: [Group 1]
Members visible to Group 2: [R&D, Group 1, Group 2]
3. If a member belongs to more than one department
-
If one of the departments to which the member belongs is not restricted, the member is not restricted.
For example, if Ross belongs to both Sales and Marketing Departments, and the Sales Department is restricted but the Marketing Department is not, Ross can still view all contacts.
-
If the departments to which the member belong are all restricted, the visible range is the union of rules.
Rule 1: The Sales Department can view the Personnel Department and Lily.
Rule 2: The Marketing Department can view R&D Department.
So the final visible range for Ross is [Personnel Department, R&D Department, Lily].
Member Information Display
Organization administrators can configure what information is shown when members view each other's profiles and business cards under [Org Admin] > [Security] > [Account].
-
If a member sets their phone number or email as “Visible to myself only” in [Account & Privacy], that information will not be visible to others.
-
When a member belongs to multiple departments or holds multiple positions, the system will display all associated departments and job titles.
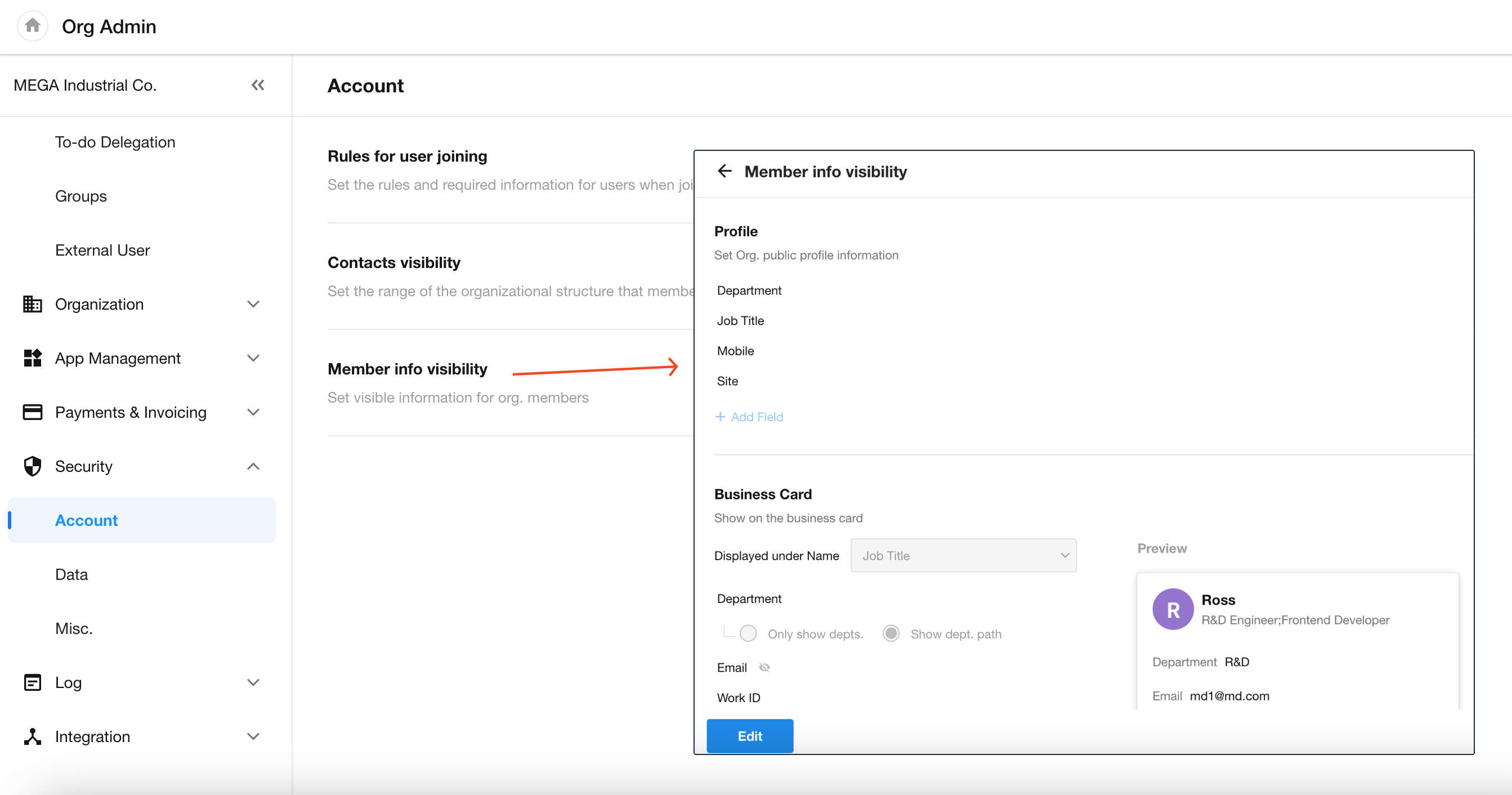
The personal profile is primarily shown when viewing the Contacts or visiting the member’s post page:
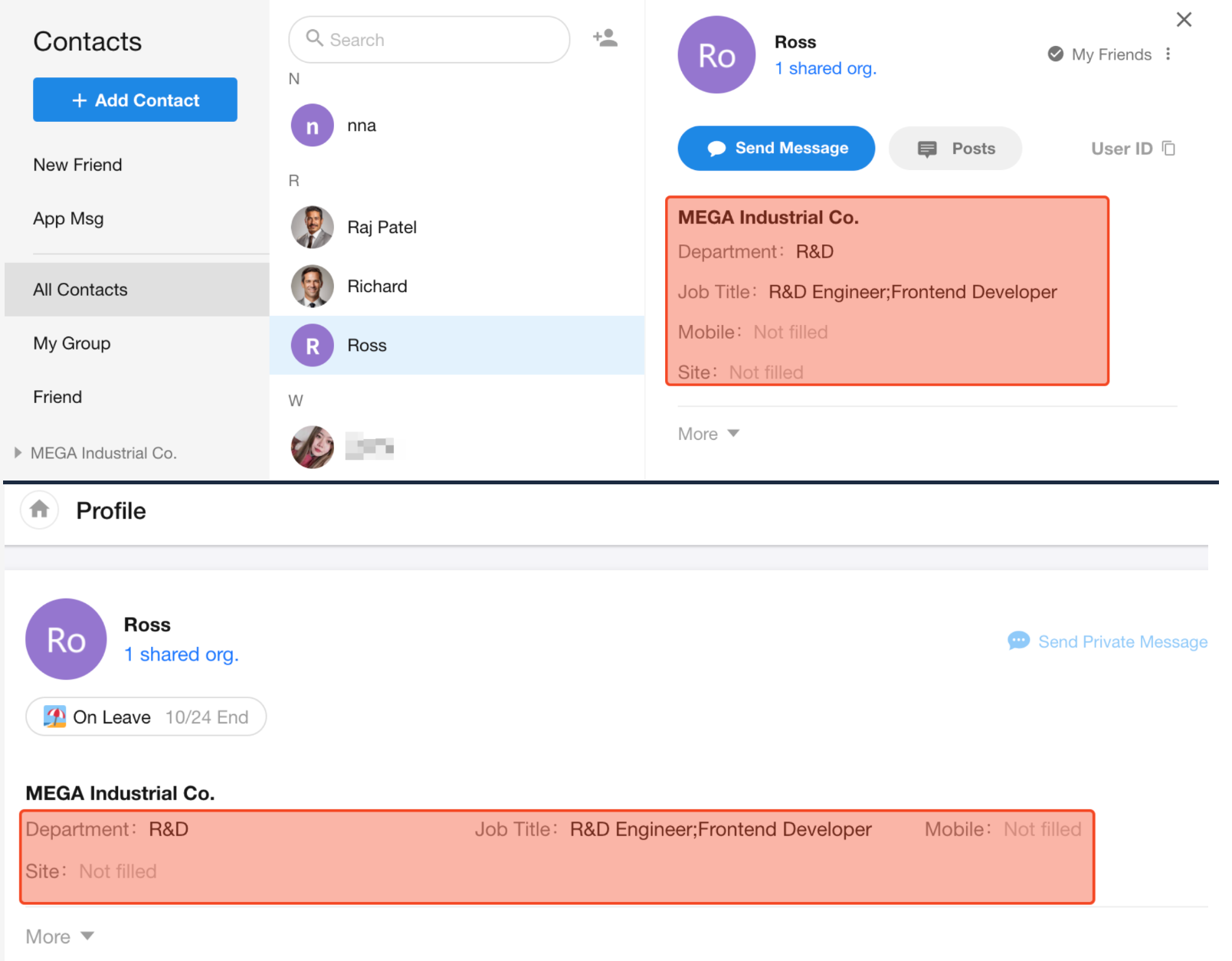
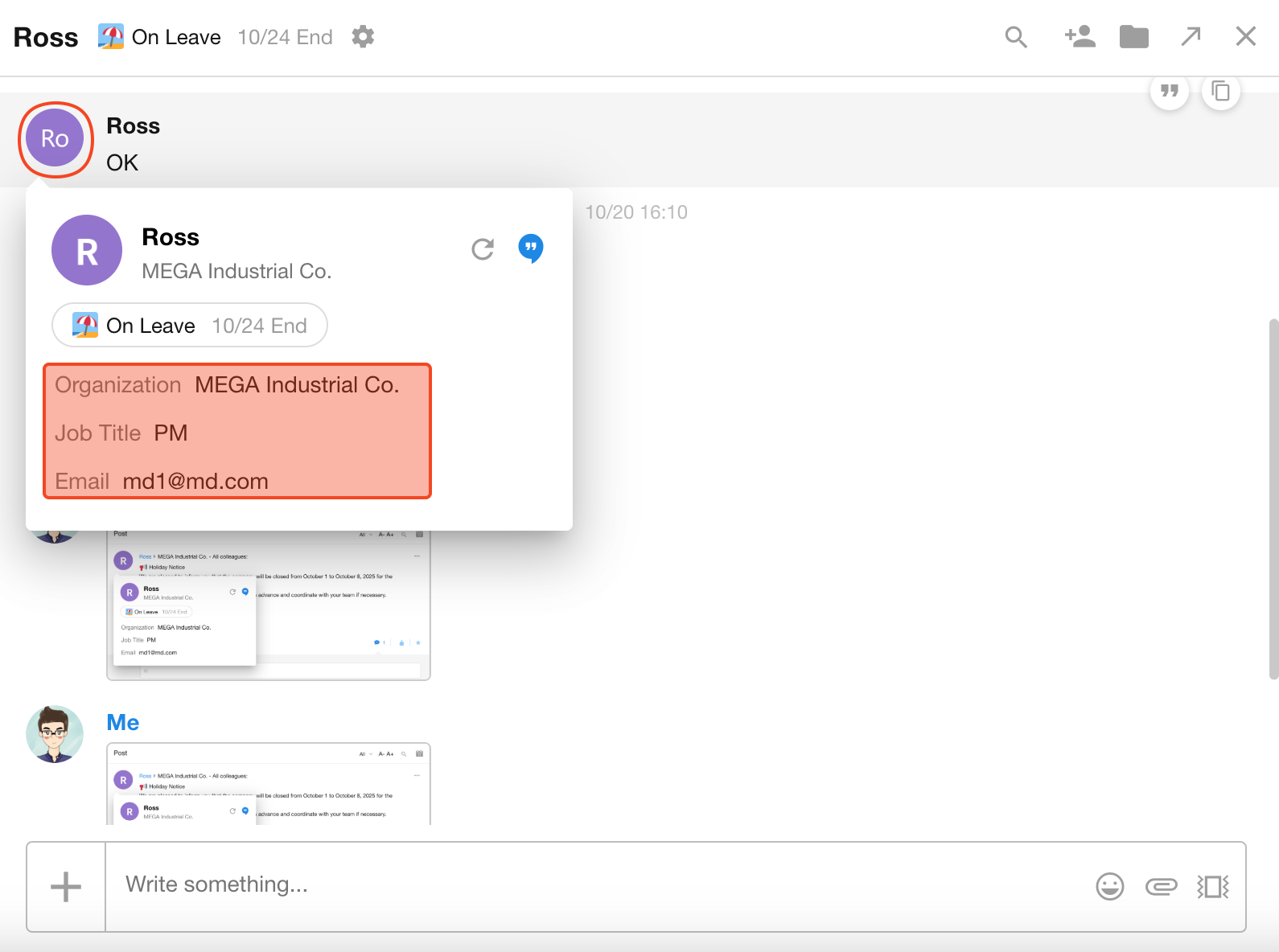
Business card refers to the pop-up information layer shown when clicking a member’s avatar within the app.
-
Fields that are left empty will not be displayed.
-
The Department field supports two display modes:
- Show only the department name
- Show the full department path
Screen Watermark
To enhance enterprise data security, screen watermarks can be enabled on the organization management console, app views, and worksheet pages.
Enable / Disable Watermark
Organization admins can click the profile avatar and navigate to [Org Admin] > [Security] > [Data] to toggle the watermark setting.
The watermark can include combinations of the user's name, phone number (last 4 digits), email, and organization name.
You can also input a custom fixed string—up to 20 characters.
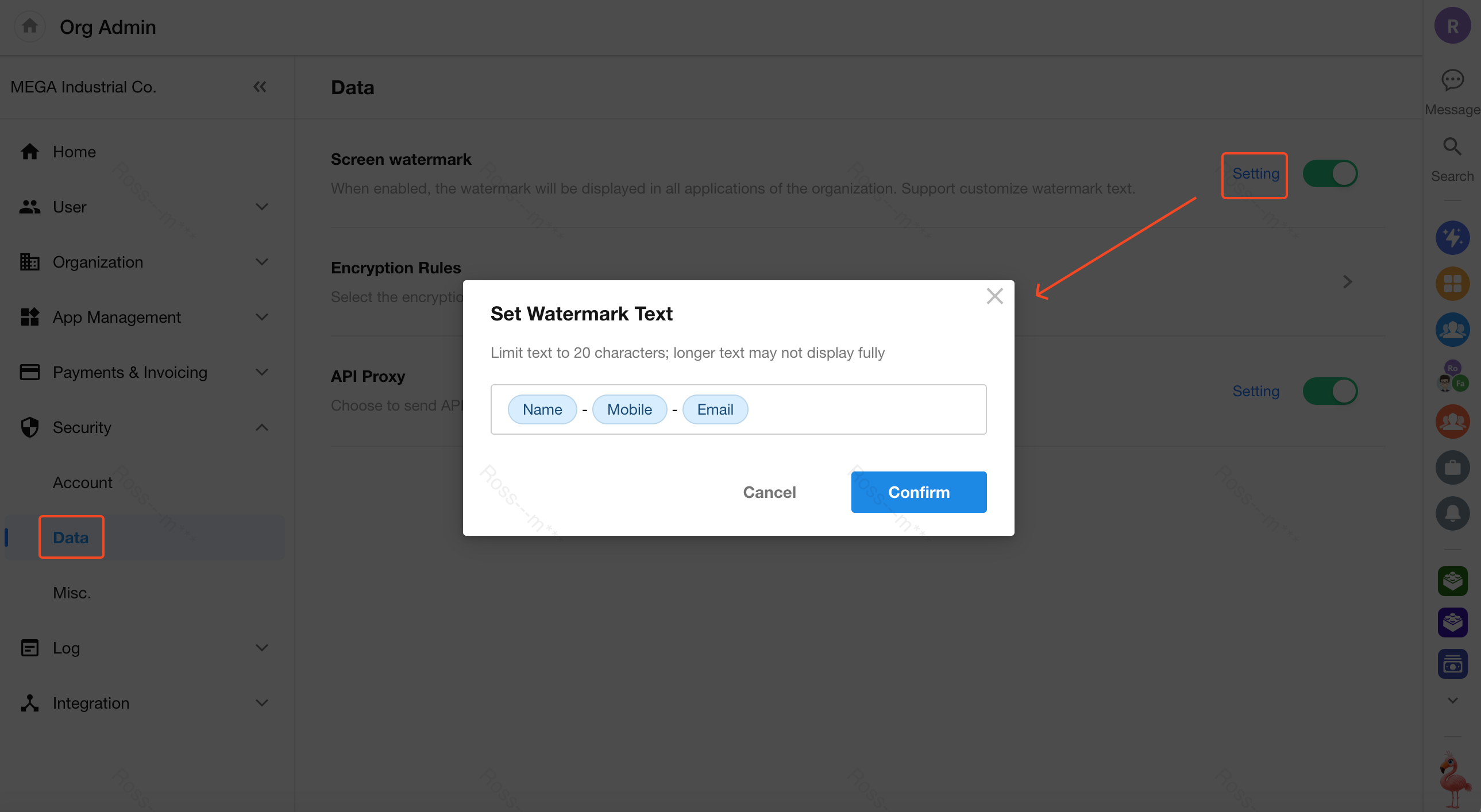
Watermark Display
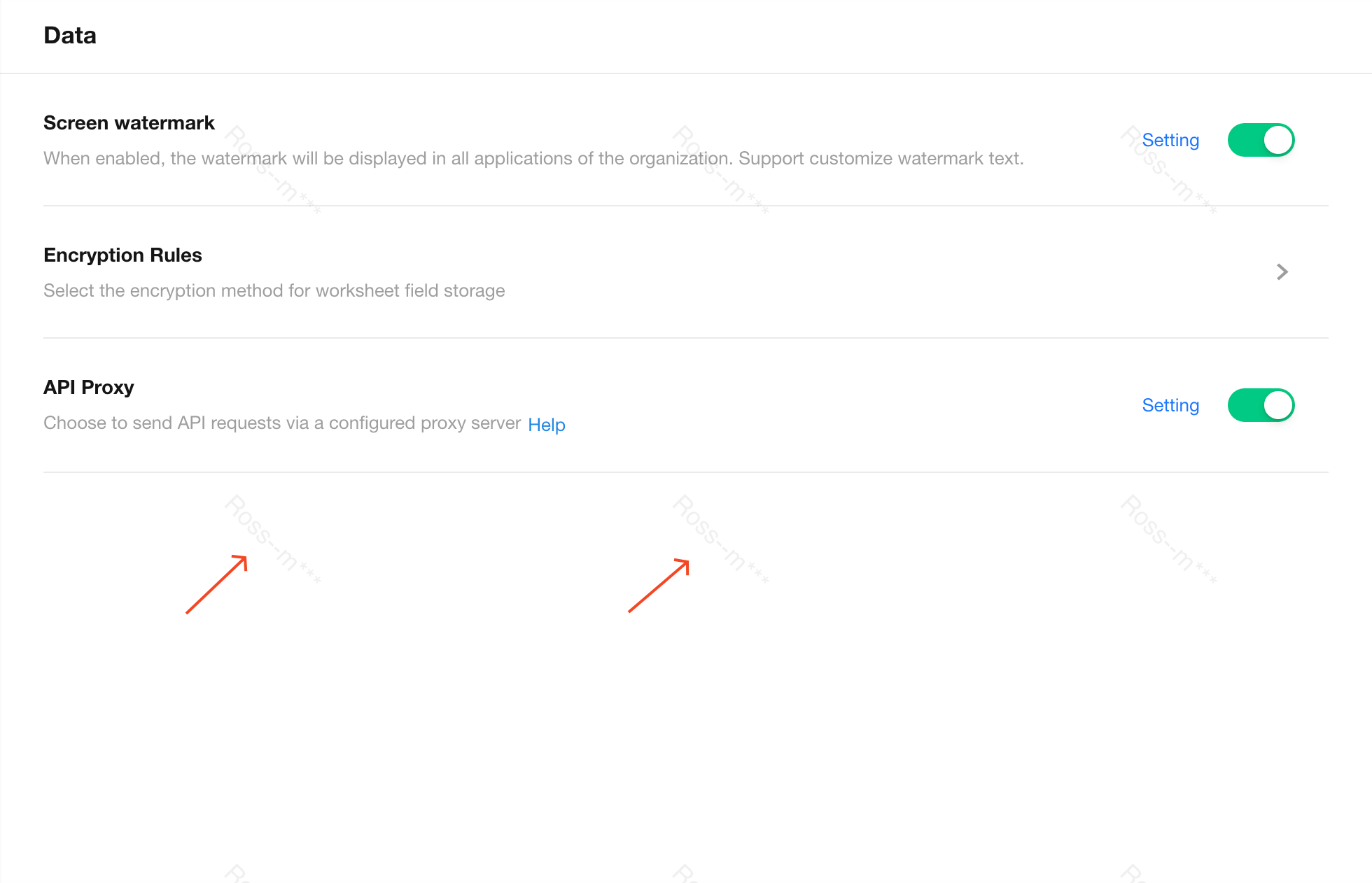
Where the Watermark Appears
Watermarks are shown on selected pages only:
-
All pages in the Organization Management Console
-
App pages where user data is displayed:
- Home page
- Record creation page
- Record editing page
- View pages (record list)
- Custom pages
Watermark is retained when custom pages are saved as images
- User Management (including External Portal Management)
- Workflow list page
Watermarks do not appear on form configuration or workflow configuration pages within the app.
Preview and download of images in attachments also support watermarking. Learn more
Field Encryption Rules
Some business data involves sensitive information that may require encryption, such as customer account numbers, ID numbers, bank card details, phone numbers, emails, and passwords. Once encrypted, the data is stored in ciphertext in the database and decrypted for display according to defined rules.
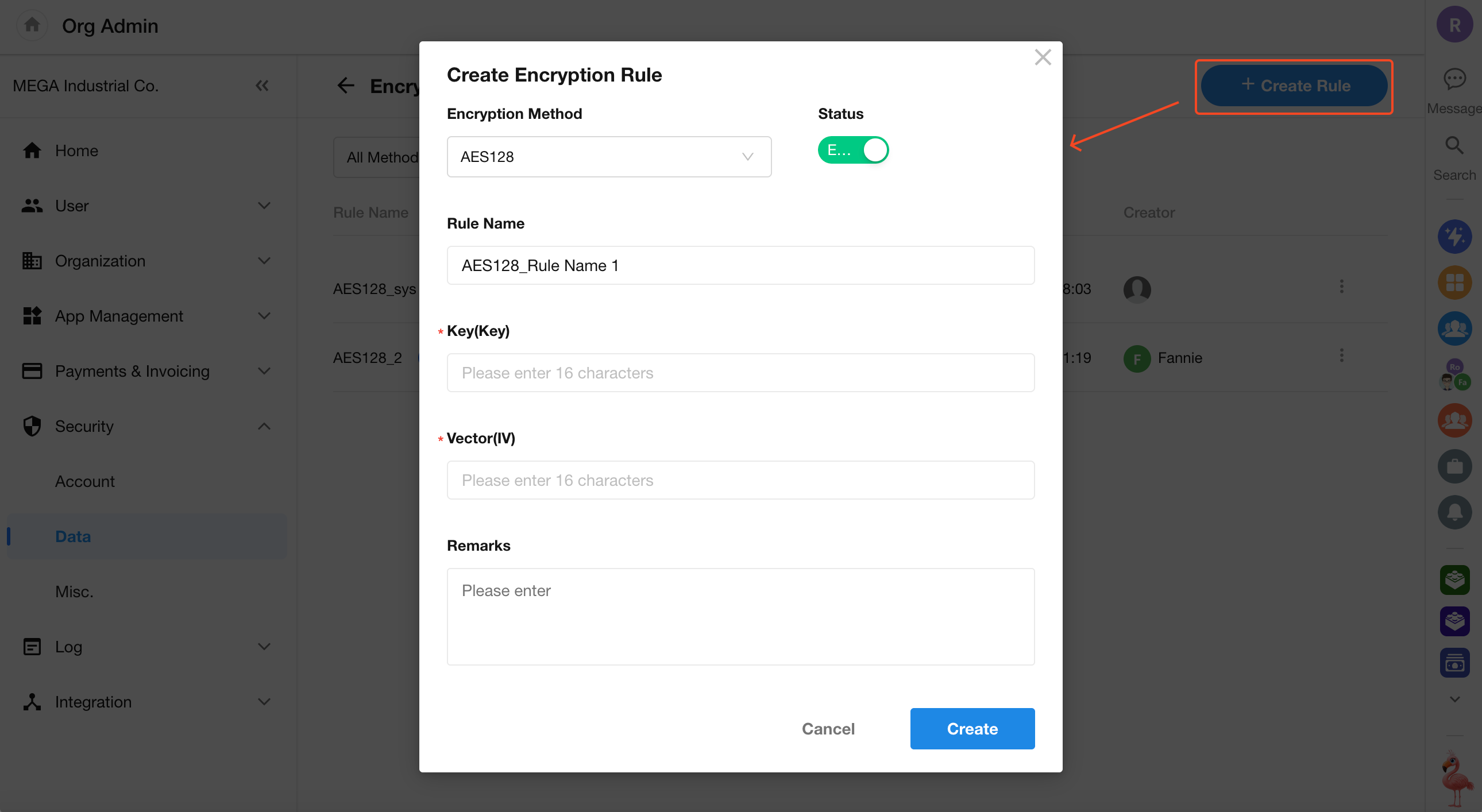
Create an Encryption Rule
Before applying encryption to fields, an organization admin must configure encryption rules.
To create a new encryption rule:
Go to [Security] > [Data] > [Encryption Rule] to create and manage encryption rules.
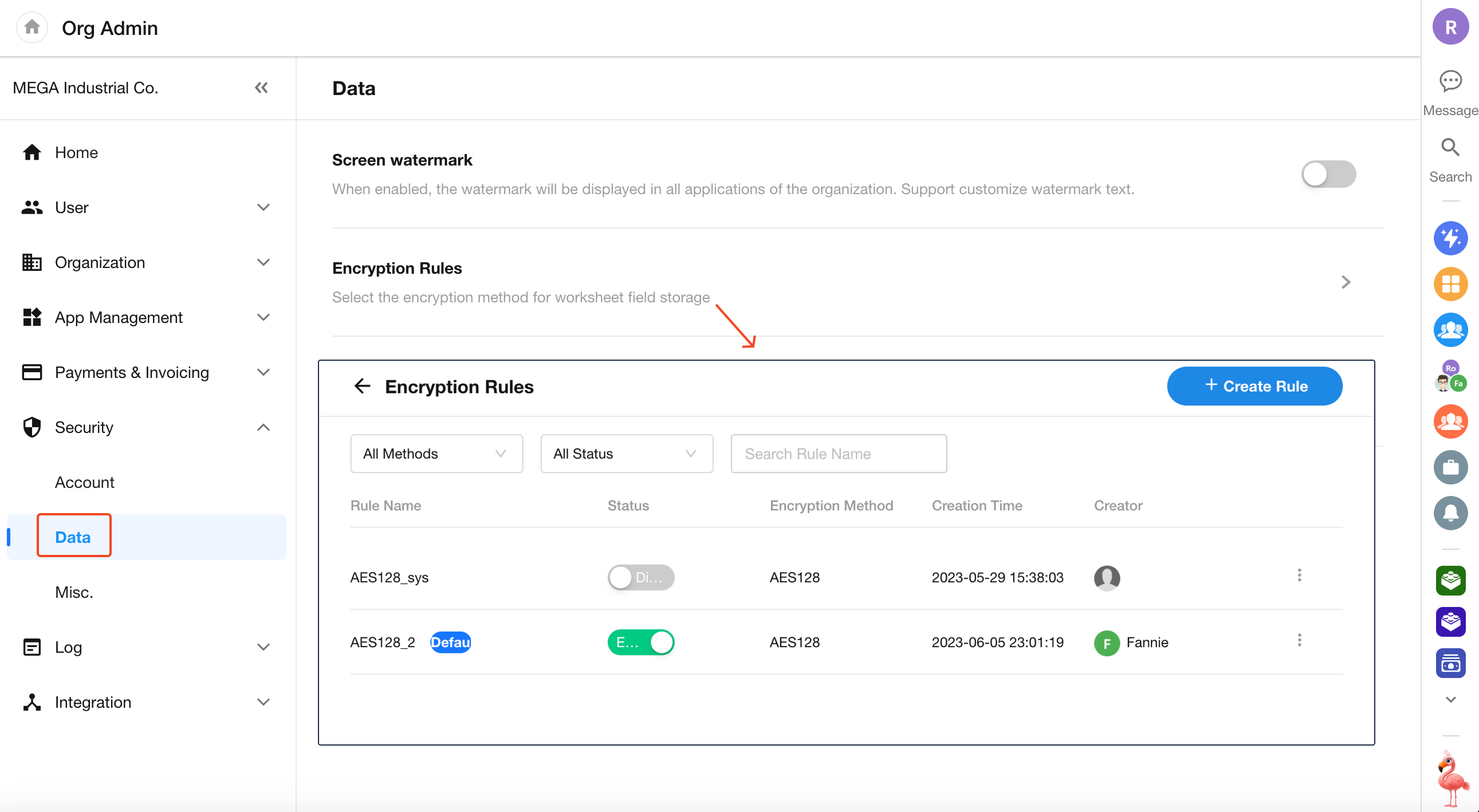
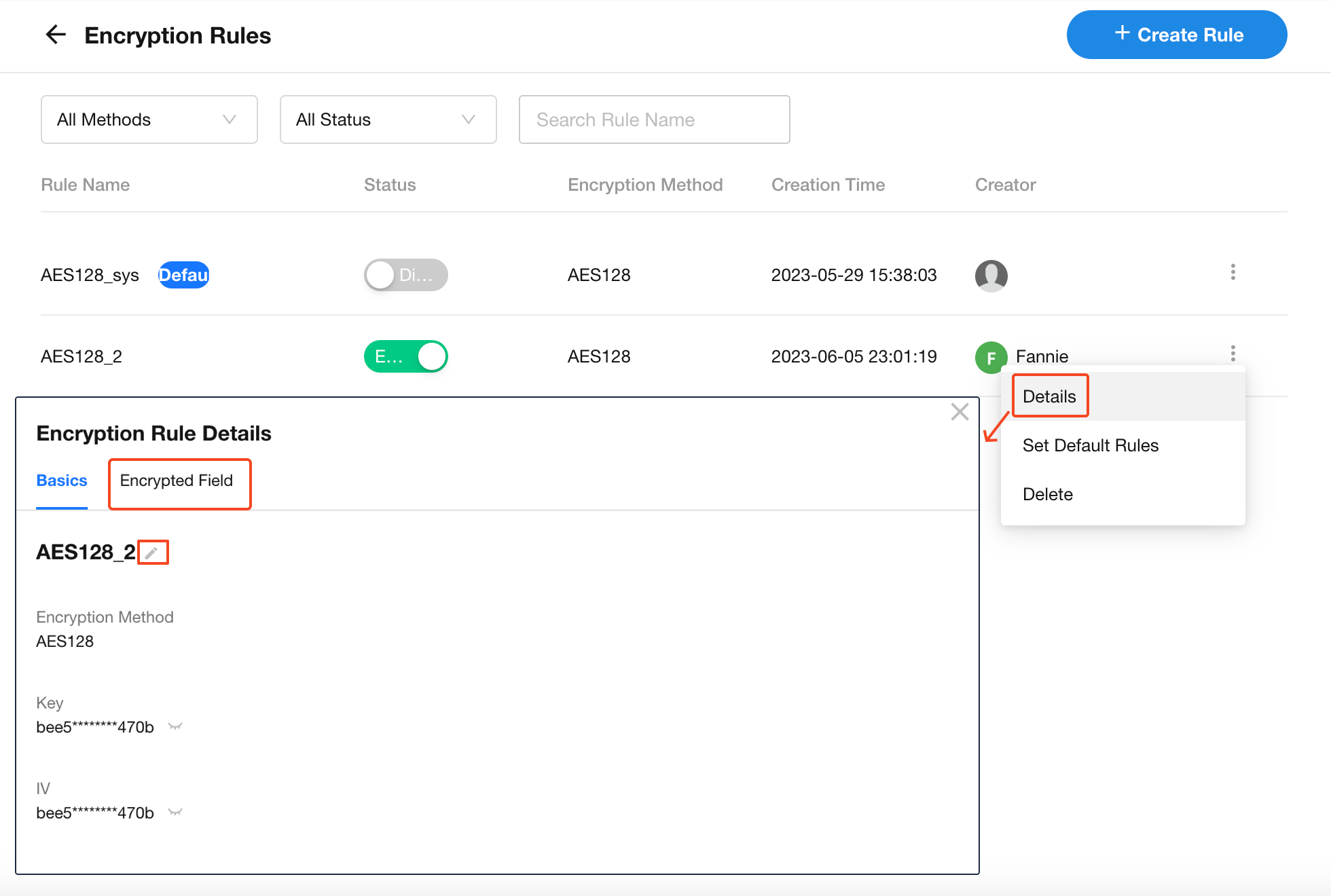
Each rule includes the encryption method and encryption key. Multiple rules can use the same method.
HAP supports four encryption methods: AES128, AES192, AES256, and SM4.
Manage Encryption Rules
Each organization is automatically provisioned with a default encryption rule (using AES with a randomly generated key).
Super admins can create additional rules by specifying the encryption method and key.
- System-generated rules cannot be modified or deleted
- You can designate a default encryption rule
- Rules can be enabled or disabled
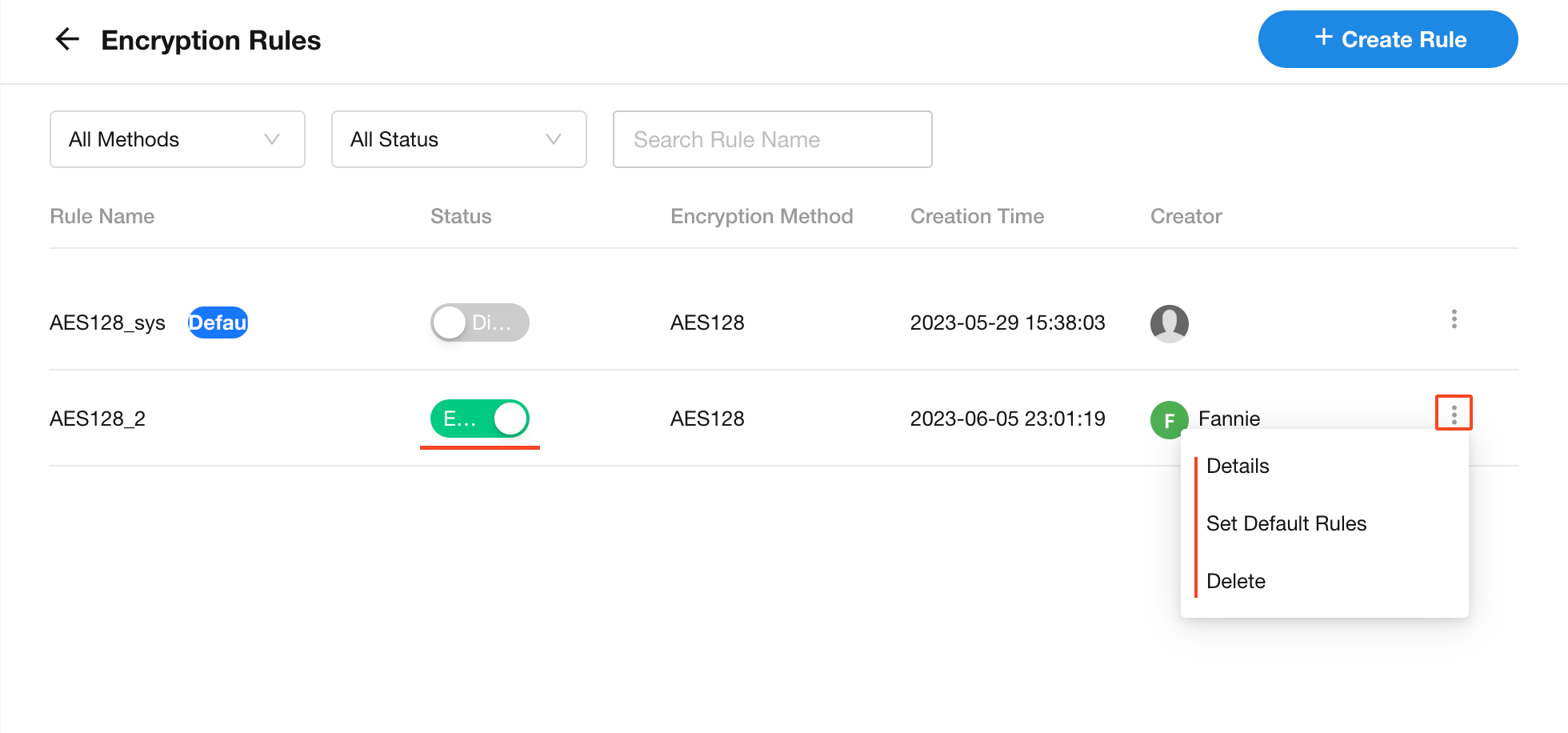
For individual rules, you can edit the rule name or view all fields using that rule.
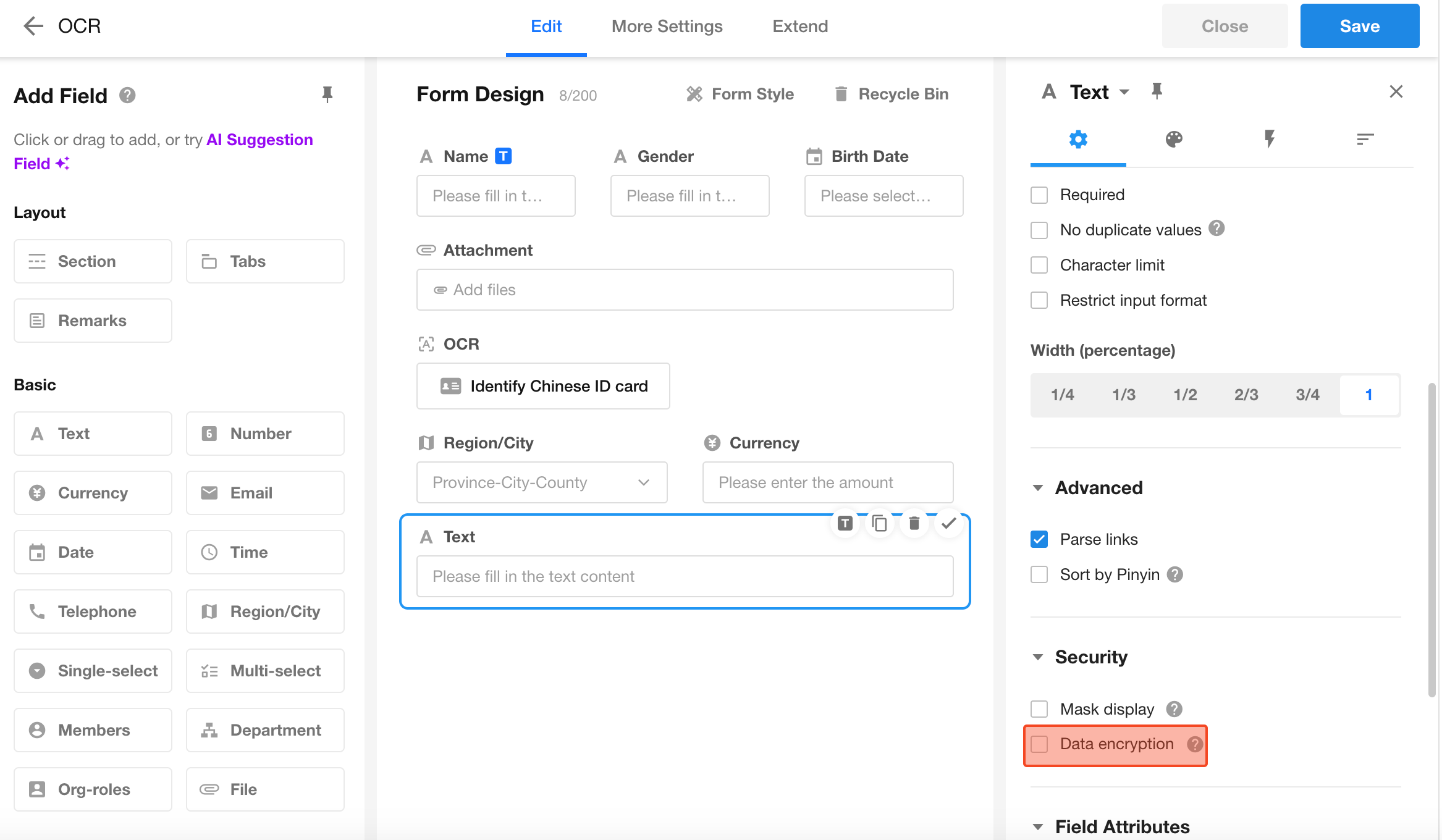
Apply Encryption Rules to Fields
Once encryption rules are configured, they can be applied to fields in a worksheet.
Learn more about field encryption
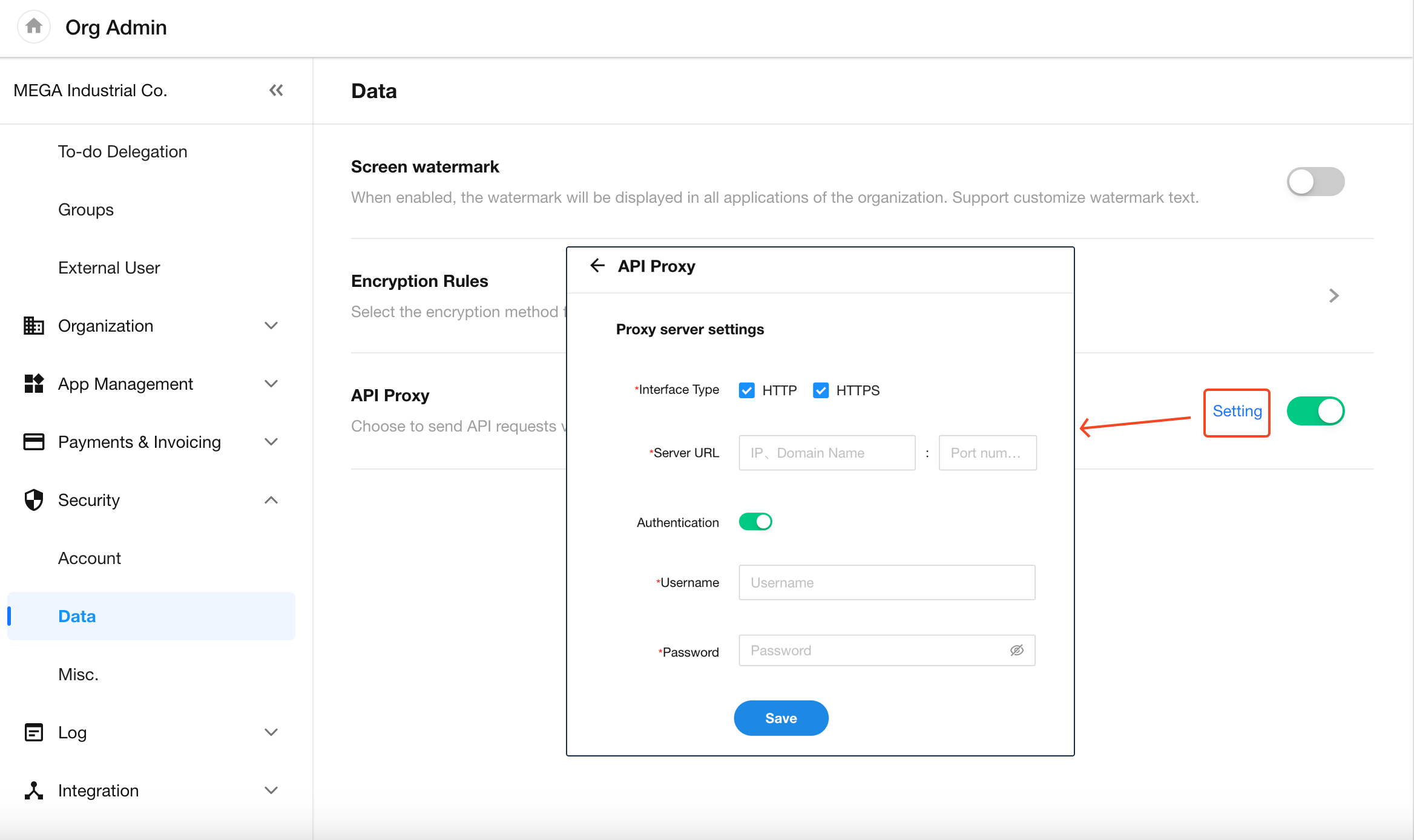
API Proxy
Organization administrators can configure an API network proxy to route API requests from internal apps through a designated proxy server.
Enable and Configure
Go to [Org Admin] > [Security] > [Data], and toggle on API Proxy. Then click Setting to configure the proxy information.
Note: If the proxy server is only configured for HTTP, HTTPS requests will bypass the proxy, and vice versa.
Where the Proxy Can Be Used
-
"Send API Request" node in workflows
-
API request settings in Integration Center
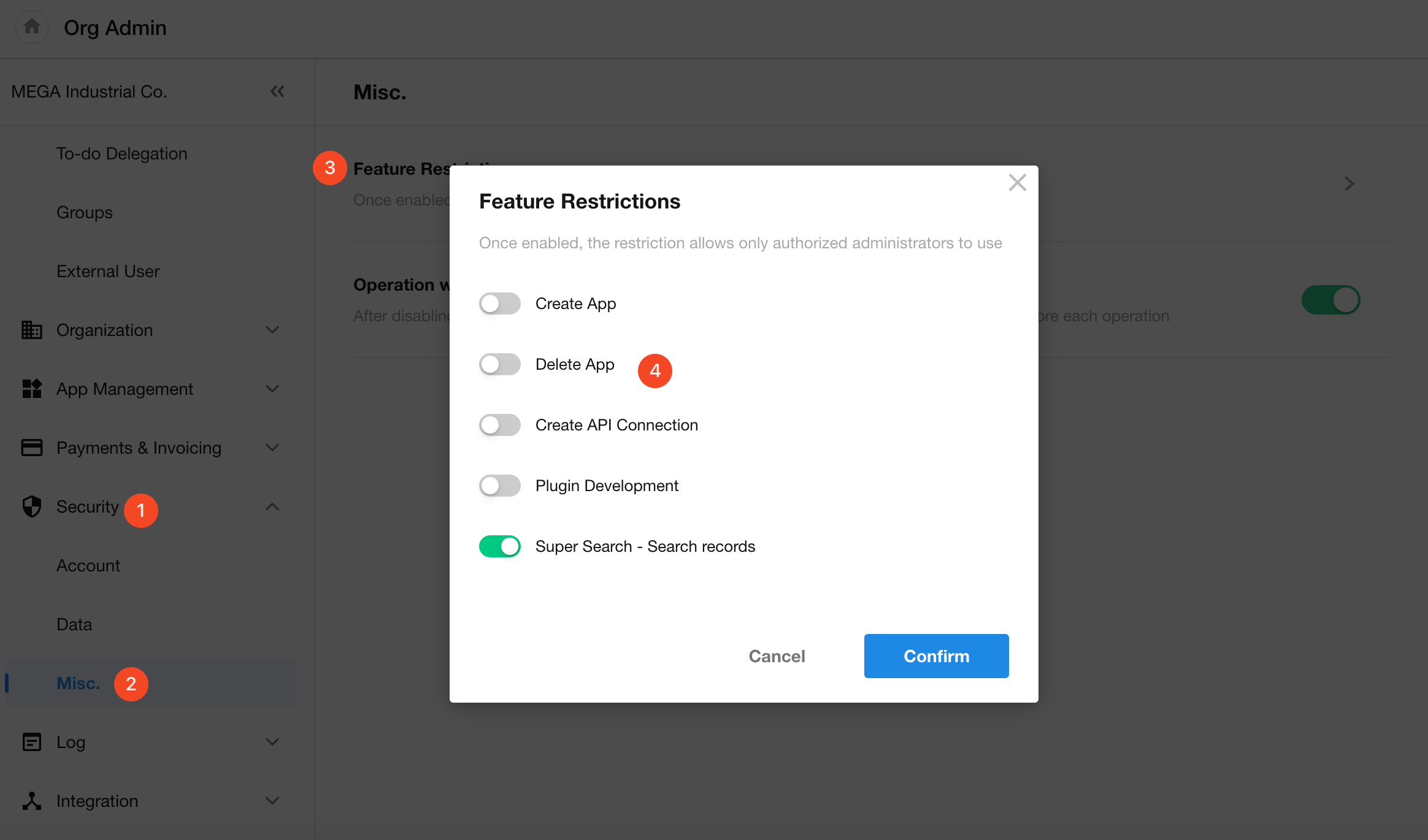
Feature Restrictions
Some features can be restricted to app administrators only, including:
- Creating new apps
- Deleting apps
- Creating API connections
- Developing plugins
- Performing record search in Super Search
Go to [Org Admin] > [Security] > [Misc.] > [Feature Restrictions] to enable or disable each item in the popup window.
By default, all restrictions are disabled, meaning all members can access the features. When enabled, only app administrators can perform the corresponding actions.
When record search in Super Search is disabled, it is unavailable for all users.
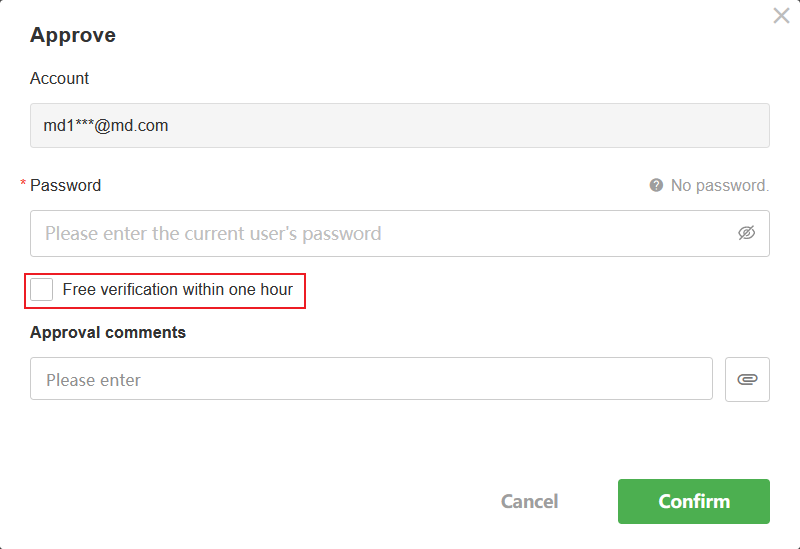
Passwordless Verification
You can allow passwordless operations within approval flows or custom buttons after the user has authenticated once within 1 hour.
-
When enabled:
Users can check the option "Skip password verification within 1 hour" after verifying once, applicable across all approval and custom button operations that require login password. -
When disabled:
Password verification will be required every time before performing such operations.